Until recently, most people did not question what became of a hard disk drive (HDD) when a computer was scrapped. But with millions of hard disk drives retired every year, there are many documented incidents of sensitive private data becoming public when the HDDs resurfaced in the secondary market. Now, due to rising concerns of identity theft and with stricter regulatory compliance guidelines, it is more crucial than ever for data on HDDs as well as other forms of media containing sensitive data to be properly sanitized.
Fujitsu created the Mag EraSURE™ line of degaussers to help companies and organizations quickly and securely erase data on hard disk drives and other types of magnetic media. To demonstrate the product’s effectiveness, Fujitsu engaged the services of DriveSavers, the worldwide leader in data recovery services, to see if they could recover any data from a set of leading-edge, high capacity Fujitsu hard disk drives that had been degaussed by the Mag EraSURE product. After extensive testing, the company certified that the Mag EraSURE P2V device had rendered the data on the HDDs unrecoverable by commercial means.
Your Risk in Today’s Business Environment
According to a leading market research firm, the hard disk drive industry shipped nearly 220 million hard disk drives in 2002. It is also estimated that the typical HDDs life span is five years. With an average of seven hard disk drives expect to be retired for every ten shipped, this means that by 2007, almost 154 million hard disk drives will have been retired. A large number of these hard disk drives will not be destroyed, but will instead end up in the secondary market.
There are several documented cases of organizations entrusted with confidential information that neglect to properly sanitize an HDD before disposing of the computer. For example, in August 2002, the U.S. Veterans Administration Medical Center in Indianapolis eliminated 139 computers. While most were donated to schools, others ended up in the open market. It was later discovered that many of these computers contained the names of veterans who had AIDS or who were suffering from mental health problems. In addition, 44 credit card numbers used by the Veterans Administration were also found on these systems.
Because of incidents like this, Fujitsu created the Mag EraSURE line of degaussers* to help companies and organizations erase data on hard disk drives and other types of magnetic media before disposing of them.
Technology
Erasing magnetically recorded data via degaussing may be accomplished in two ways: AC erasure and DC erasure. With AC erasure, the media is degaussed by applying an alternating field that is reduced in amplitude over time from an initial high value (i.e., AC powered). For DC erasure, the media is saturated by applying a unidirectional field (i.e., DC powered or by employing permanent magnet technology).
The Mag EraSURE P2V product, which has been designed for commercial as well as industrial use, is a DC erasure product and uses an array of permanent magnets. Composed of the rare earth elements NdFeB and arranged in a patented structure, the permanent magnets within the Mag EraSURE device creates an intense magnetic field without requiring any type of electrical charge.
A degausser is a device that can generate a magnetic field for degaussing magnetic storage media. Degaussing is the process of reducing or removing an unwanted magnetic field. It is named after Carl Friedrich Gauss, an early researcher in the field of magnetism.
Additionally, the back yoke structure realigns the stray field and further concentrates these fields by what is known as the “Mirror Effect”. With this technology, the Mag EraSURE P2V model is able to focus the degaussing field to the cavity area where the HDD is passed. After the magnetic media has been degaussed, data becomes unrecoverable by commercial recovery services.
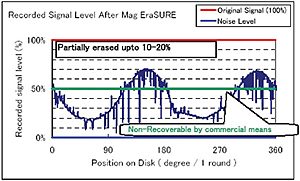
Figure 1: Graphs of a hard disk drive with 5000 Oe before and after a single pass through the Mag EraSURE P2V device. After degaussing, a significant amount of recorded signal has fallen below the read/write head readable level.
How Mag EraSURE works
The degausser field effect on magnetic media can be further illustrated through Applied Physics:
As magnetic media passes through the high-energy magnetic field H, the number of flux lines inside the material is increased by its relative permeability (µr), defined as:
The retention of flux density B, after a field has been removed, is called “Remanence Br” (measured in Wb/m2 or Gauss).
The field strength of the opposite polarity required to reduce this remanence to zero is termed the coercive force of coercivity Hc (A/m or Oersted).
Ferroelectric materials are characterized by magnetization curves and hysteresis curves (see Figure 2).
Consider a piece of ferromagnetic material (e.g. media from an HDD) that is originally unmagnetized (a). As the external magnetic field (H) is increased, the induced magnetization (M) also increases. The induced magnetization eventually saturates (b). The curve between points (a) and (b) is called the magnetization curve. If the external field is reduced, the induced magnetization is also reduced, but it does not follow the original curve. Instead, the material retains a certain permanent magnetization, known as the remanent magnetization Mr (c). The remanent magnetization is the permanent magnetization that remains after the external field is removed. This is how the hard disk drive creates its data bits.
If the external field is further reduced, the remanent magnetization will eventually be removed (d). The external field for which the remanent magnetization goes to zero is called the coercivity Hc. The product Mr (infinity) x Hc is termed the strength of the magnet.
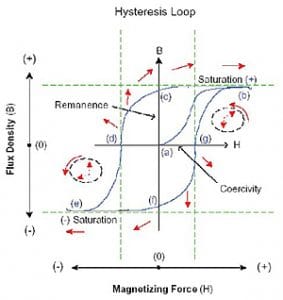
Figure 2: As the external field continues to reverse, permanent magnetization of the opposite polarity is created in the magnet. A similar curve is traced for the negative direction with saturation (e), remanent magnetization (f) and coercivity (g). The hysteresis curve then retraces points (b) to (e) as the field cycles.
In magnetic recording, the media is often not completely saturated. The external magnetic fields (H) are held below the maximum fields for saturation, and the induced magnetization (M) is correspondingly less. Thus, the induced remanent magnetization is less that the maximum Mr.
The hysteresis loop can also be applied to explain how the Mag EraSURE device erases data on magnetic media. As the media travels through the magnetic field of the device, the magnetic field of the media (H) will be fully saturated, causing all data bits to flip in the direction of the external magnetic field of the Mag EraSURE degausser. This flipping of data bits occurs in both the data and servo area of the media. Once the data and servo data has been permanently flipped in a uni-direction*, then this information can no longer be detected, or read, by the hard disk drives’ read back head.
 Before Degaussing
Before Degaussing
 After Degaussing
After Degaussing
Figure 3: Photos of HDDs with the recorded data track before and after being degaussed by the Fujitsu Mag EraSURE device.
Because Fujitsu was so confident that its Mag EraSURE P2V model would effectively destroy hard disk drives, the company extended a challenge to a leading commercial data recovery service to see if they could rescue any information on a set of HDDs once they had been degaussed by the Mag EraSURE product.
The recording polarities on the media are written in a North or South direction to identify a logical ‘0’ and ‘1’.
Commercial Recovery Services
DriveSavers, the global leader in the data recovery industry since 1985, is one of the most progressive and experienced specialists in the industry. Physically damaged HDDs, from broken actuators to failed controllers, are regularly handled by their cleanroom technicians.
DriveSavers’ cleanroom engineers inspect, analyze and assemble hard disk drives in the same type of specialized environment as the products were manufactured. When the mechanics of a hard disk drive fail, the damaged unit is only opened in a dust-free lab, known as a cleanroom, to avoid media corruption and contamination and to maximize recovery results.
At DriveSavers, an ASA 100 cleanroom is used to perform data recovery. The ultra-clean work areas are certified, with fewer than 100 air contaminant particles per 0.5 micrometers per foot allowed to circulate through the air, 50,000 times purer than our everyday environment. As added protection, cleanroom technicians wear a special suit, hair cap, mask, boots and latex gloves at all times.
Fujitsu sent DriveSavers three of its 300GB Enterprise hard disk drives, which feature four platters, 4200 Oe media filled with 279GB of data. Before delivery to the data recovery company, the HDDs were first degaussed by the P2V product in the following manner: one unit was erased in a single pass with the PBA up; another unit was degaussed in a single pass with the PBA down; and the final HDD received two passes, one on each side. Initial testing in the clean room revealed that each HDD had malfunctioned and made a clicking sound as it spun.
Full testing and data recovery attempts were performed on all three hard disk drives, including an examination of the media and head stack with a high-powered microscope, plus disassembly and testing of the internal components. After the disassembly and the replacement of the head stack and actuator assembly, DriveSavers engineers verified that the media of all units was intact and that there was no physical damage (i.e. head crash). In addition, no debris was found on the heads or media surface.
Whitepaper
During power-on, the hard disk drives exhibited a repetitive clicking as they attempted to calibrate and read maintenance tracks and servo data. However, because the HDDs were degaussed, no servo data (head positioning data) could be located, causing the units to continuously recalibrate and fail to boot up.
DriveSavers final conclusion was that all media surfaces appeared to be in pristine condition, but the hard disk drives were completely unrecoverable due to missing servo data. Without the servo data, the HDDs could not properly read the media and complete a data recovery. Based on this testing, DriveSavers certified that no commercial software utility program or data recovery service company would be capable of recovering data from any of the hard disk drives that had been erased by the Mag EraSURE P2V product, regardless of the resources devoted to the effort.
Summary
The success of the Fujitsu Mag EraSURE degausser in erasing data on the hard disk drives confirms the P2V models’ status as the ultimate tool for secure data disposal. The low maintenance Mag EraSURE product is a cost-effective solution for any industry dealing with large amounts of highly confidential information, including legal, medical and financial markets. Users can be confident that the magnetic media degaussed by the Fujitsu Mag EraSURE device will be securely destroyed.
Whitepaper
References
1. C. Mee and E. Daniel, “Magnetic Recording”, Volume I, McGraw Hill, 1988, pg 3.
2. C. Mee and E. Daniel, “Magnetic Recording”, Volume III, McGraw Hill, 1988, pg. 155.
3. Finn Jorgensen, “The Complete Handbook of Magnetic Recording”, First Edition, Books, 1980, pg 30.
4. Garfinkel, Simson L., and Abhi Shelat. “Remembrance of Data Passed: A Study of Disk Sanitization Practices.” IEEE Computer Society January 2003. 23 Oct. 2006 http://www.computer.org/portal/site/security/menuitem.6f7b2414551cb84651286b10 8bcd45f3/index.jsp?&pName=security_level1_article&TheCat=1015&path=security/v1 n1&file=garfinkel.xml&
5. Hasson, Judi “V.A Toughens Security After PC Disposal Blunders,” Federal Computer Week, August 26, 2002. Oct. 19, 2006 http://www.fcw.com/article77509-08-26-02-Print
About Fujitsu Computer Products of America, Inc.
Fujitsu Computer Products of America, Inc. is a subsidiary of Fujitsu Limited, a leading provider of customer-focused IT and communications solutions for the global marketplace. FCPA provides innovative solutions for the U.S. marketplace. Current product and service offerings include high performance hard disk drives, Magneto-Optical drives, scanners and scanner maintenance, palm vein recognition technology, 10Gb Ethernet switches and degaussers.
Fujitsu Computer Products of America, Inc.
http://us.fujitsu.com/fcpa
1255 East Arques Avenue, Sunnyvale, CA 94085-4701. (800) 626-4686 (408) 746-7000 info@fcpa.fujitsu.com
©2006 Fujitsu Computer Products of America, Inc. All rights reserved. Fujitsu and the Fujitsu logo are registered trademarks and The Possibilities are Infinite and Mag EraSURE are trademarks of Fujitsu Ltd. All other trademarks are the property of their respective owners.
All statements herein are valid only in the U.S. for U.S. residents, are based on normal operating conditions, are provided for
their performance specifications, availability, price, and warranty and post-warranty programs.



 WESTBOROUGH – With data breaches and identity theft growing concerns, a local company is betting many companies will want to have their old electronic equipment turned into unrecognizable shreds.
WESTBOROUGH – With data breaches and identity theft growing concerns, a local company is betting many companies will want to have their old electronic equipment turned into unrecognizable shreds.

 Before Degaussing
Before Degaussing After Degaussing
After Degaussing